MDM Vs EMM Vs UEM- What’s the difference?
What’s the difference between mobile device management, enterprise mobility management, and unified endpoint management? Find out
SIGN-UP FOR SUPEROPS.AIHere's the thing, mobile devices matter, and keeping track of them has never been more important. There's a lot of industry guidance available, with mobile device management (MDM), enterprise mobility management (EMM), and unified endpoint management (UEM) being the key players in endpoint management. Endpoint management is the process of monitoring and authenticating endpoint devices to block unauthorized threats and attacks. These mobility management solutions address data security, threat protection, and privacy concerns. However, they vary significantly, so in this blog, we're going to look at MDM, UEM, and EMM.
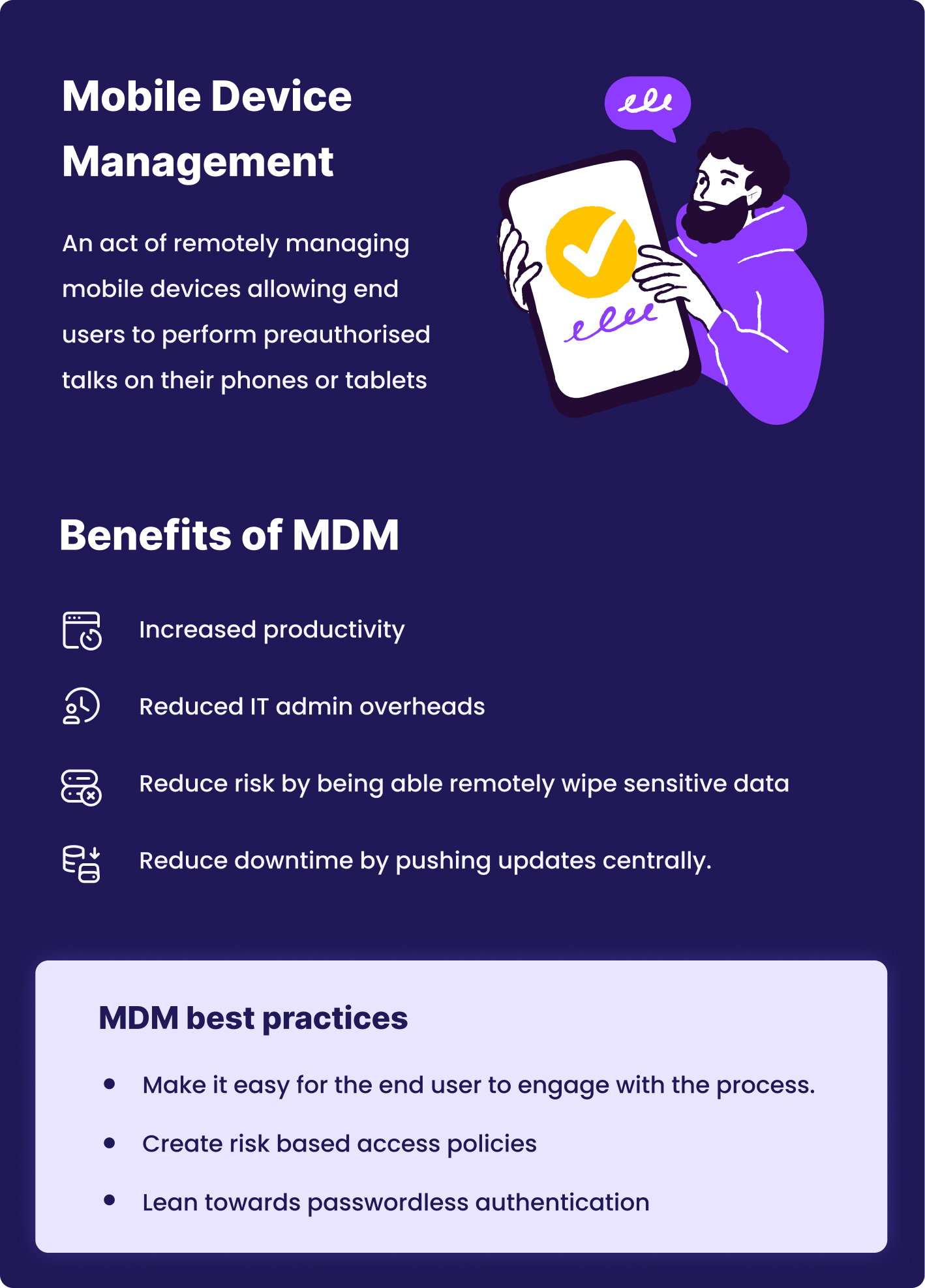
Mobile Device Management
MDM is the practice of remotely managing mobile devices allowing end users to perform pre-authorized tasks on their phones and tablets. MDM typically provides features like enrollment, device provisioning, device security, and location tracking, and it can also be used to wipe data from the device if it's lost or stolen. MDM tools' functionality typically includes tracking inventory, providing real-time monitoring, and enforcing security policies.
MDM Benefits
An MDM solution can help organizations manage devices and data effectively. Other benefits of MDM include:
Increased end-user productivity by giving end-users the option to carry out tasks on mobile devices rather than PCs or laptops.
Reduced IT admin overheads as your support teams can support mobile devices remotely.
Reduce risk by being able to remotely wipe company data from a device if it's lost or stolen.
Reduce downtime; the IT department can remotely install or push updates centrally, meaning that colleagues will always have the latest, most stable version of the ap.p
MDM best practices
When designing an MDM strategy:
Make it easy for the user to engage with. The #UX is different when using a mobile device, and your users expect a seamless experience. If you force end-users to engage with security measures that make logging difficult, they'll look for ways to circumvent the process. It'll also be more difficult for your service desk technicians to provide support. Look for password-less login functionality to make it easy for your users to use the tool.
Create risk-based access policies that grant and limit authorization based on who is logging in, the device they're using, and the security posture of that device. A risk-based policy will check for potential security risks every time a colleague tries to log in. For example, checking if the mobile device has been updated, or checking for anomalies in the login, for example, logging in from a new location or if the person is accessing new information.
Lean into passwordless authentication. By implementing passwordless authentication, you strengthen multi-factor authentication by using a less secure factor (like passwords or PINs that can be guessed or cracked) and replace it with biometrics, a safer option.
Enterprise Mobility Management
EMM is the set of people, processes, and technology focused on managing mobile devices, wireless networks, and any other mobile computing services in an enterprise context. EMM levels up from MDM as it increases the scope from phones and tablets to mobile computing services and incorporates aspects of mobile access management (MAM) to protect applications and their data, therefore, incorporating support for Bring Your Own Device (BYOD.)
EMM Benefits
Benefits of EMM include:
Support for BYOD - a game changer for many. Some colleagues won't want to have separate phones for work and personal tasks, so support for BYOD allows people to work from their devices of choice.
Reduced tech overhead as not all colleagues will need (or want) a separate work device.
Greater choice for colleague.s
Management of both mobile and stationary devices.
Collection of usage analytics.
More nuanced control of corporate applications.
The ability to set corporate policies remotely.
EMM Best Practice
When looking at how EMM could support your business, consider the following:
Lean into automation; look for opportunities to automate governance and admin controls to make support tasks and remote admin easier and less intrusive for end users.
Enforce the principle of least access privilege, ensuring that each colleague can only access the resources necessary to perform their job to protect corporate data from external threats.
Encrypt devices, apps, and data to protect your organization's data and its people.
Build data security policies to protect against device loss, jailbreaking devices, and potential vulnerabilities.

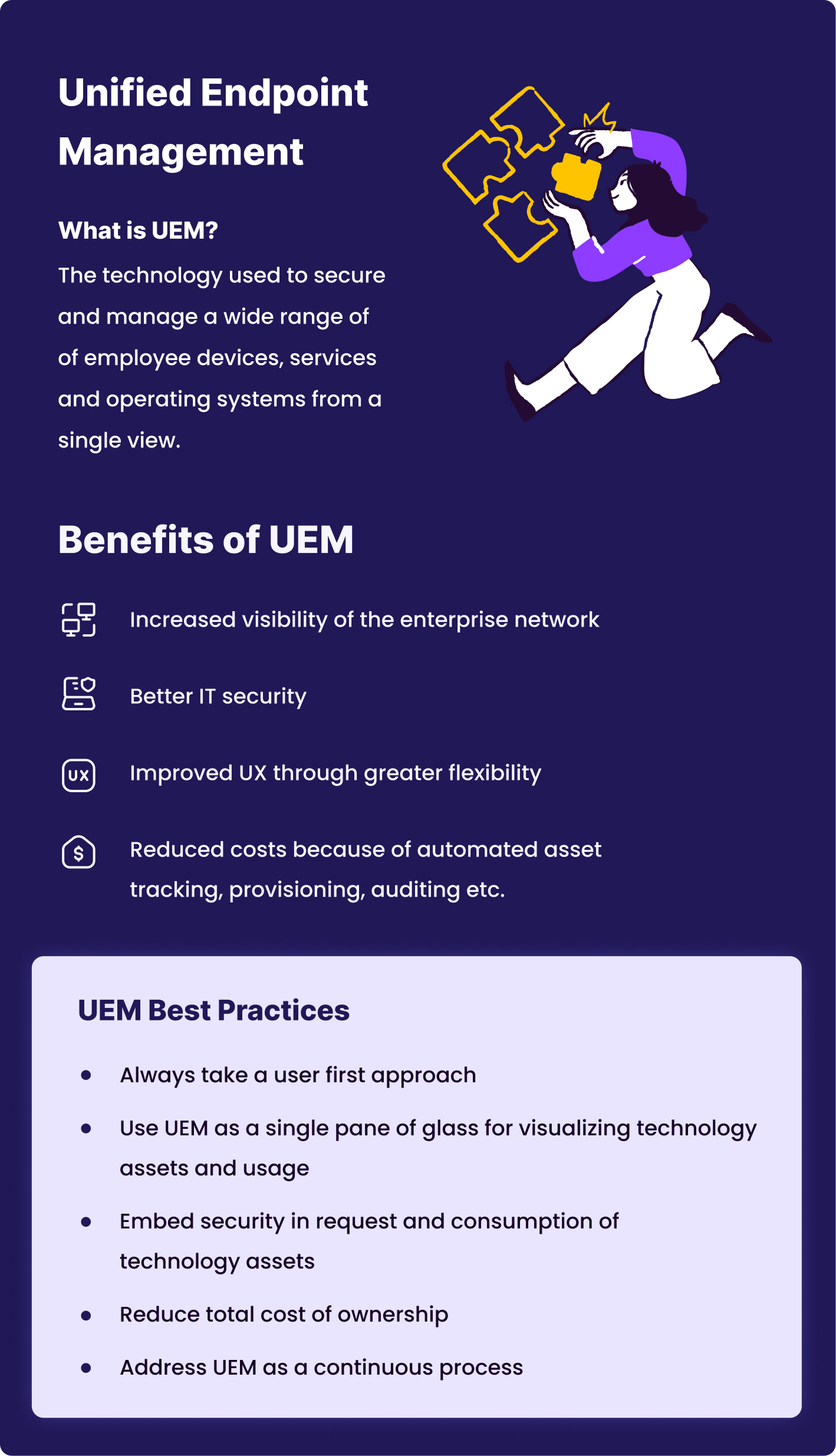
Unified Endpoint Management
UEM describes the technology used to secure and manage a wide range of employee devices, services, and operating systems, all from a single view. Just as EMM levels up from MDM, UEM includes all the capabilities of EMM and allows IT to manage multiple endpoint types, including Windows. iOS, Android, Chrome OS, and Mac OS. In addition, UEM solutions provide users with access to all their apps and files. Typical UEM solutions enhance the scope of device management and include capabilities such as endpoint management (obviously), threat detection, mitigation and remediation capabilities, security updates, software and OS deployment, patch management, device compliance, remote control options, and remote wiping of lost or stolen devices.
UEM Benefits
The most significant benefit of UEM is the ability it gives organizations to manage, control, and protect their environments from one unified service. Other benefits include:
Increased visibility of the enterprise network. Because UEM can support multiple endpoints and device types, it promotes a more comprehensive view of your estate, allowing IT to monitor inventory, threats, vulnerability information, and data usage.
Better IT security as a centralized approach lets IT manage security and track threats across all endpoints and devices from a single system.
Improved #UX through greater flexibility.
Automation reduces administration costs as related IT tasks such as endpoint inventory, asset tracking, provisioning, auditing, and data recovery can all be done remotely through a single service.
Better decision-making because UEM enables administrators or asset managers to view and analyze the data produced from endpoint devices. Most UEM solutions will offer diagnostic and predictive tools that analysts can use to process and interpret data. This data can discover threat events enabling your support teams to act accordingly. The increased transparency will make it easier for decision-makers to manage data, generate reports customized to business requirements and make informed decisions.
UEM Best Practice
When looking at UEM, some best practice ideas to include are:
Start with the user. When planning for UEM, borrow the voice of the customer concept from lean sigma so that your solution is easy to use and engage with.
Consider your service ecosystem platform agnostic, with your UEM tool acting as a single pane of glass for visualizing technology assets and usage.
Embed security in the request process, as well as the consumption of technology assets.
Ensure a pre-agreed level of security on all devices and provide support for additional levels of protection for select groups and devices where appropriate.
Automate processes to lower the total cost of ownership (TCO).
Address UEM as a continuous process. UEM isn't a "one and done" silver bullet. Devices will continue to evolve, so your UEM tool and supporting processes will need to adapt to support business needs.
Try the next-gen UEM software for modern MSPs
All tools. One place. Make endpoint management software a breeze with SuperOps